Personal information is becoming increasingly valuable. Not only to the companies who rely on it to conduct business, but also to cybercriminals.
A quick Google search reveals that individual data records themselves are sold at around $200 each—scale that to hundreds of thousands of individual records, and a singular security breach can translate to a hefty payday.
Recent data (as we will see below) shows that the financial services sector (including revenue-based financing) is becoming a major target for cybercriminals. Criminals make money by selling the information they take, and by using the financial information itself.
There are a lot of factors at play here, but one major one is the continued focus of financial services organizations on digital transformation. While organizations have increasingly left behind slow, inefficient, and siloed legacy systems, they haven’t been as vigilant about prioritizing cybersecurity and adequately assessing the risk associated with new technology.
In this article, we’ll examine the importance of cybersecurity in the financial services sector, and for MCA funders specifically, and cover some best practices that can protect your funding business and your customers.
Cybercrime in Financial Services
Criminals are developing more sophisticated tactics to steal data from businesses or hold their data hostage in exchange for ransom. It’s getting increasingly difficult to decipher organizational and workflow vulnerabilities.
In terms of general numbers, in 2023 the global average cost of a data breach was $4.45 million. On average, a data breach in the financial services industry costs almost $6 million—28% more than any other industry—and there have been more than 20,000 attacks over the last 20 years.
Because of the potential for a massive payout due to gaining access to highly sensitive information, those companies that provide consumer and/or commercial capital are much more susceptible to cybercrime than other organizations within financial services. Again, a lot of factors at play here, but a big one is the vulnerable cybersecurity posture of third-party vendors crucial to most lending/funding businesses.
Skeptical? Check out the recent data breach of Financial Business and Consumer Solutions (FBCS).
The Bank for International Settlements puts it this way:
“The digital transformation of finance also introduces–or heightens–cyber risks… the attack surface is broadening, however, as interconnectivity increases and the disaggregation of services introduces more links to each product chain and user interface.”
MCA funders, as stakeholders in the financial services ecosystem that depend on interconnectivity, are also a target.
Three Common Cybercrime Attacks
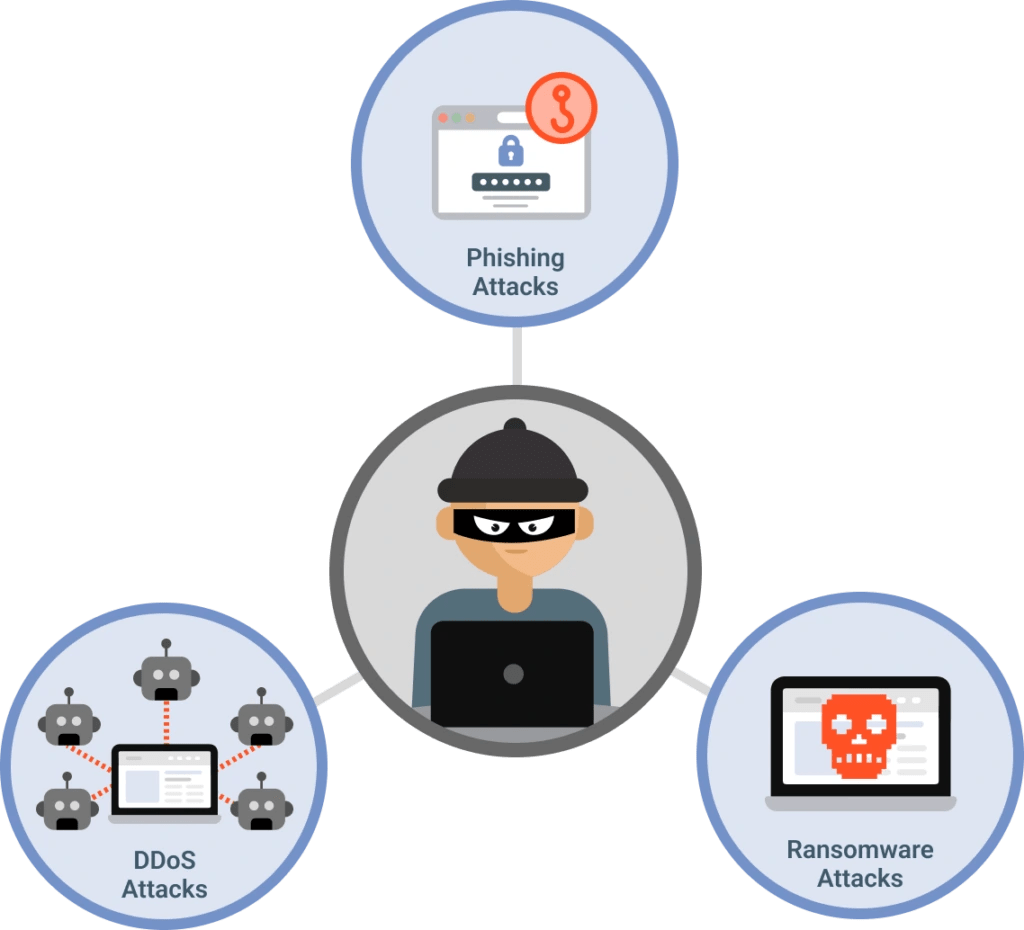
Combating cybercrime can only be successful if you know what to look for. Everyone who operates in the digital realm, and especially in the financial services sector, should be aware of these three common cyberattacks.
1. Phishing Attacks
Phishing attacks involve an attempt to gain login credentials for access to an internal network. Most commonly, these attacks take place via email where a message that looks legitimate is sent to a user with a link that initiates the installation of malware on the internal system.
These emails look authentic and are difficult to recognize as an attack. At least 80% of cyberattacks are initiated via a phishing attack.
2. DDoS Attacks
DDoS stands for Distributed Denial of Service. In a DDoS attack, cybercriminals overwhelm a server with fake connection requests, forcing it to go offline. By disrupting the normal flow of web traffic, like a traffic jam, devices can be compromised and controlled remotely for nefarious purposes.
3. Ransomware Attacks
Ransomware attacks can instantly freeze an entire organization’s funding operations. Cyber criminals steal sensitive data and then hold it hostage, extorting the company and threatening to publish the information if a ransom isn’t paid.
The financial services industry is particularly vulnerable to ransomware attacks because of its valuable consumer information and heavy regulatory environment. Because of this, many funders may feel pressure to comply with any demands to supposedly limit the potential damage.
Cybercrime Will Cost You
Cybersecurity is today’s version of a bank vault. Rather than a physical armed guard, today’s digital funding businesses need to rethink their security budgets and focus on more advanced defenses.
Waiting until it’s too late can be costly in more ways than you anticipate. There will undoubtedly be financial ramifications to deal with, not to mention the downtime/disruption and the reputational hit your funding business will take.
Here are a few ways your MCA funding business can suffer financial losses in the aftermath of cybercrime.
1. Recovering Compromised Data
First there is the cost of recovering breached data. Unfortunately, these issues can’t be resolved overnight.
On average, it takes over 230 days to identify and contain data breaches for financial services organizations. The consequences of criminals having unfettered access to customer data for such long periods of time are dire.
2. Fines and Legal Fees
Everyone in the financial services industry, including MCA funders, is held to some degree of regulatory accountability, with high stakes for non-compliance in the form of fines and penalties.
The Federal Trade Commission (FTC) holds companies that legally handle personal information even more accountable for how they manage such sensitive information. It can charge up to $46,517 in civil penalties per violation.
These fines, penalties, and settlements can be financially devastating, as evidenced by the infamous Equifax data breach of 2017 and the Experian data breach of 2020. For Equifax, the total assessed in fines and settlements amounted to an estimated $575 million—nearly 20% of their $3.41 billion revenue for 2017.
3. Contractual Obligations and Compliance
The regulatory environment for MCA funders can be complex, and this complicates matters in the event of a data breach. The FTC and your customers will pay attention to the fine print when it comes to your contractual obligations.
In most cases, the organization responsible for holding the sensitive data is liable for damages. Your contractual obligations to your client may be monetary or involve identity theft monitoring. If left unfulfilled, there could be an additional significant cost associated with every customer involved in a data breach.
In addition to these examples, it’s again important to remember the stigma of a successful cyberattack on your organization: it’s sure to raise red flags for current and future investors and customers.
The industry is slow to forget negative news, and a data breach can quickly result in the decline of your funding business. Not only will you lose existing customers, but new customers will also steer clear.
5 Best Practices to Prevent Cybercrime
Your MCA funding business is worth defending. How? Here are five actionable defensive tactics to deploy to safeguard it.
1. Train Your Employees
Your staff is the gatekeeper to sensitive information. Because the nature of cyberattacks continually changes, it is important to annually conduct information security training. This training should cover things like:
- How to spot phishing and other common attacks.
- The social engineering tactics that attackers use.
- AML/KYC policy review.
Virtual learning sessions, quizzes, and even phishing tests can be powerful methods to train your employees.
Talk to them about the importance of their role in keeping customers safe. Discuss their responsibilities and set clear policies (for example, sharing passwords should never happen) regarding how data is to be handled. Be sure to limit administrative access to vital systems, and conduct regular training sessions teaching your employees to spot scams.
2. Keep Software Updated
Putting off an update on any device leaves your business vulnerable to attacks. Maintaining the latest version of software is the easiest step you can take to defend against attacks.
Why?
Because software providers with a strong information security program abide by current vulnerability, threat, and patch management policies to ensure they are aware of the latest threats and can consistently patch or update software to fix vulnerabilities. Be sure to incorporate any software updates into your workplace policies as part of your cybersecurity strategy.
3. Back Up Important Data
Hackers stealing information can be problematic in more ways than one. Downtime for your organization doesn’t have to be one of them if you have regularly backed up your data. This means that at any point, your entire system can be restored to a previous point in time.
How frequently should you conduct backups? As often as possible. For most businesses, it’s at least once a day, but several times a day will offer further insulation against potential disruption.
The most secure way to back up your data is to ensure that it is done on a regular basis and is stored in a remote location, off-site and off-server. Review your data backup procedure with your IT provider to ensure your data backup is adequate for your MCA funding business to continue to operate if files are corrupted, stolen, or lost.
4. Only Use Trusted Software and Secure Websites
Few things are more enticing than a “free” program to download that promises to quickly solve a problem. Similarly, unsecured websites can easily allow access to stored passwords or browser history. Only secure websites should be accessed on work devices.
All programs that are utilized for work purposes need to be appropriately vetted and approved. Ask your IT provider or in-house team for a list of approved software and educate your staff on website security.
Most browsers will display a warning if a user is attempting to access a non-secure website (one without an SSL certificate), but this can be easily dismissed in a click or two. Give your staff examples and teach them to pay attention to these warnings and immediately exit the browser if one is displayed.
5. Deploy a Cloud-Based Funding Platform
Even with a highly trained IT department, cybersecurity is an ongoing, evolving threat. Rather than engaging in a game of whack-a-mole with every threat that pops up, be proactive in your cybersecurity efforts by deploying a cloud-based funding platform like Onyx IQ.
Contrary to some of the SaaS security myths out there, this technology does not pose an inherent risk. A SaaS funding platform is elastic, taking much of the burden of investing in security and regular upgrades off of your shoulders.
This type of funding platform takes comprehensive measures to protect your information from loss, unauthorized access, and destruction through firewalls, encryption, access authorization controls, and secure data backups without any additional steps from your staff.
Onyx IQ Can Be Your Digital Defense
Designed for MCA funders, Onyx IQ has the cybersecurity features needed to help funders develop and implement a robust defense posture.
With firewall encryption, access authorization controls, and continuous security updates, your cybersecurity defense is in good hands with Onyx IQ. Want to see Onyx IQ in action? Schedule a demo today.

